Encrypt files using Gpg4win
It’s easy to encrypt files using Gpg4win. It continues to amaze me how much free, quality software applications are available on the Internet. I’ve blogged about free software a couple of years ago and plan to update that post soon. However, today I want to talk about another free application called Gpg4Win. Gpg4win is encryption software that is 100% totally free. It pretty much replaces PGP or OpenPGP which was the de-facto of encryption applications many years ago. PGP used to be free and is now owned by Symantec who does not offer a freeware version of it. However, do not fear, Gpg4win is here.
Gpg4win is a viable replacement and a quality piece of software. I’ve used it at my place of business and at home. It is easy to use and reliable. I don’t know about you, but I hate having to pay for something especially if I was able to get that “something” for free in the past. The rest of this post is about how to use Gpg4win to securely transmit your files and email to other folks. There can be a few times where you may be required to send a file or files to a customer or vendor where the data may contain sensitive info such as SSN’s or any other personal data. All you would need, to securely send that data over the Internet, is your customer or vendors public key or certificate.
Before I begin, I think a very brief introduction on how encryption works is in order. I’ll keep it very simplified. Basically, in order to encrypt a file or an email, you need a key pair which consists of a Public and Secret key. The Public key (or certificate) is meant to be shared with those who you plan to transmit and send data to. The Secret key is NEVER to be shared. The public key is used to encrypt a file while the secret key is used to decrypt a file. If you want to encrypt a file to someone, they need to send you their Public key. You then encrypt the file with “that someone’s” Public key and send it to them via FTP or another method. They are the only ones who can decrypt the file with their secret key. That is as simple as I can get it. There is some great documentation if you feel like reading more about it.
Let’s get started. The rest of this blog describes step by step on how to encrypt a file using someone else’s public key or certificate. Of course, if you so choose, you could do the opposite and send your public key or certificate to someone else which they would use to encrypt data they wanted to send to you.
Download Gpg4win at http://www.gpg4win.org/. Accept the defaults when installing the software. After it is installed, go your Programs, Gpg4Win folder and open Kleopatra. This is your certificate manager.
Select Import Certificates to import your vendor’s public key or certificate.
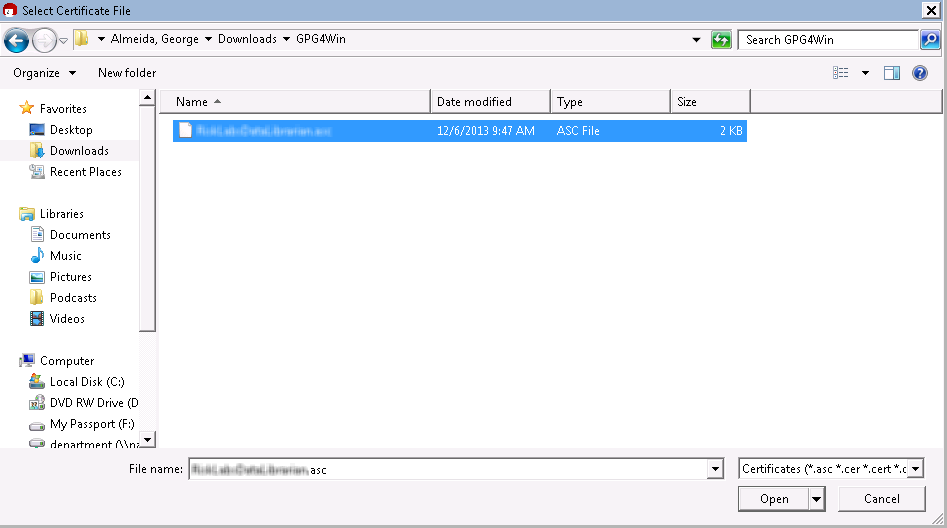
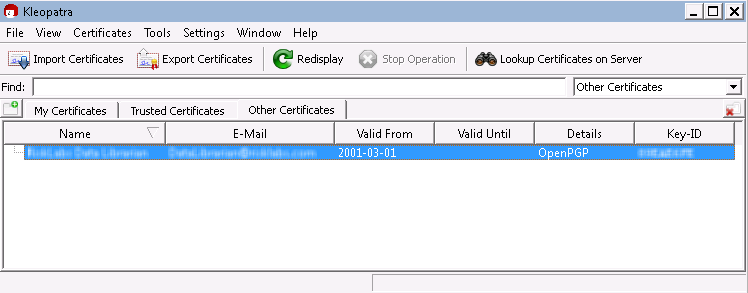
The certificate will be imported to your certificate store, also sometimes referred to as your key ring.
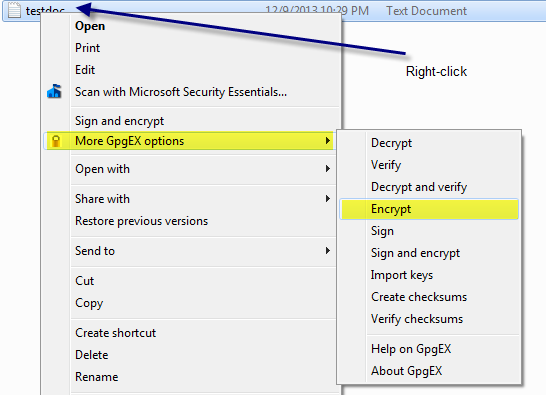
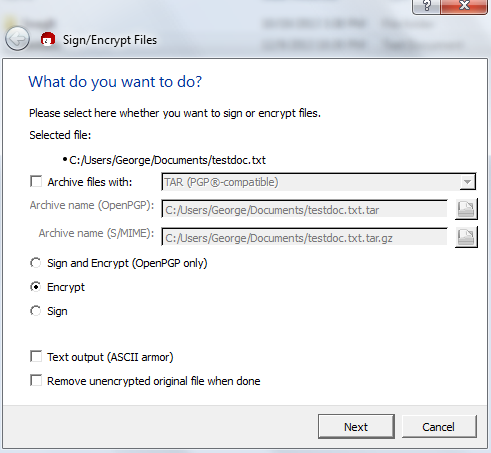
You are ready to encrypt a file or set of files to send to your vendor. Right-click on the file you want to encrypt, select More GpgEX options, then select Encrypt.
Accept the defaults and select Next.
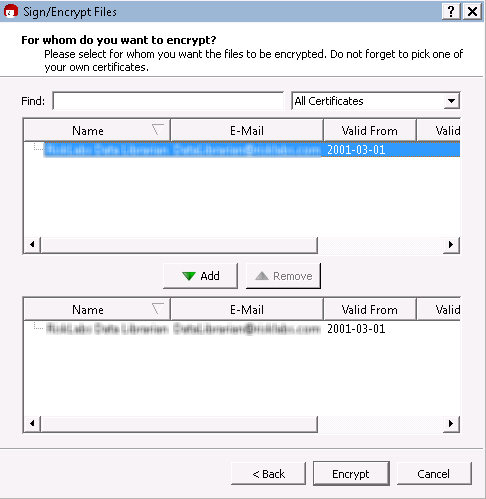
You will now be presented with your key ring with a list of all the Public keys you’ve been sent. Select the key for who you are encrypting the file for and select Add.
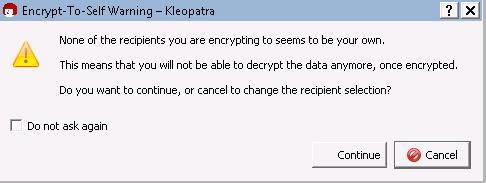
You will receive the following warning. This is OK since you are encrypting the file to send to someone else, you do not need to decrypt it therefore you do not need YOUR key or certificate to encrypt . You already have the original file. Click Continue.
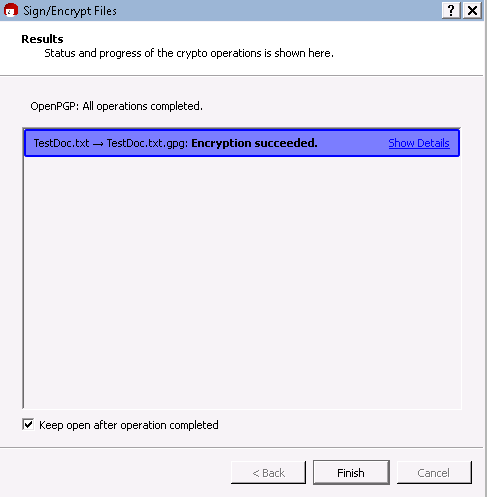
You have successfully encrypted the file. Select Finish to complete the process.
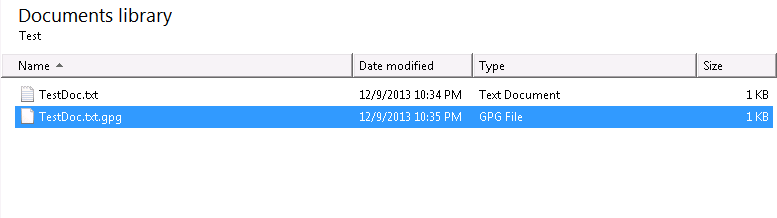
Note, a new encrypted file has been created with the extension of .gpg.
That’s it! You can now FTP this file or copy it to Dropbox or any other cloud-base storage solution and be secure in knowing that it is encrypted and only the folks it is intended for can decrypt it.
This is part I of II posts regarding Gpg4win. The next post will explain how to use the email plugin to encrypt email. Click here to read Part II – Encrypt Email using Gpg4win.




Reading this essay was a waste of time. From the title, clearly it was targeted at persons new to GPG (eg me). At the point of “Select Certificates”, you give NO example or explanation of a certificate file. You lost me at this point. I could not continue following the article without doing this. BIG ZERO
Wow. Sorry you didn’t understand but I was very clear in the post that you need the other party’s “public key” or “certificate” to ENCRYPT the data. I thought I explained it in the paragraph below: Before I begin, I think a very brief introduction on how encryption works is in order. I’ll keep it very simplified. Basically, in order to encrypt a file or an email, you need a key pair which consists of a Public and Secret key. The Public key (or certificate) is meant to be shared with those who you plan to transmit and send data… Read more »