WSUS – Automatically patch servers
Applying Microsoft security patches to servers can be a tedious and thankless job, especially if you have several hundred servers scattered all over the network. Depending on how large your organization is, this can be a full time gig……but it doesn’t have to be. In almost any IT shop, you can probably automatically apply approved updates and reboot certain servers at a specific day and time of the month. This would eliminate a server administrator from having to manually apply updates to many different servers. All you would have to do is check the WSUS reports to make sure the updates for that month were applied. Now, I know this can’t be done for all servers. Many are mission critical and may only be allowed to be rebooted a few times a year or it must be carefully scheduled. I get it. However, what if you have 300 servers around the world that you are responsible for and approximately 50% of those servers can be rebooted at certain times of the month (automatically)? You’ve just cut your patching workload in half! Now you only have to manually inspect 150 servers as opposed to 300. I don’t know about you, but I’m on board. So how do we accomplish this?
Windows Server Update Services (WSUS) in combination with Active Directory Group Policy, can easily do this for you. Before you know it, you’ll have so much extra time on your hands; you’ll finally be able to finish that Legend of Zelda game from back in the late 90’s. Just kidding……you’ll never finish it, but at least it’s more fun than patching servers. So let’s get to it.
Because each environment can vary greatly, we are making the following assumptions:
– All Server Objects exist in one single OU (i.e. Domain Servers)
– Some servers cannot be automatically patched and therefore must be omitted from the Automatic Updates process
- First, identify all your servers that can have patches applied and reboot automatically.
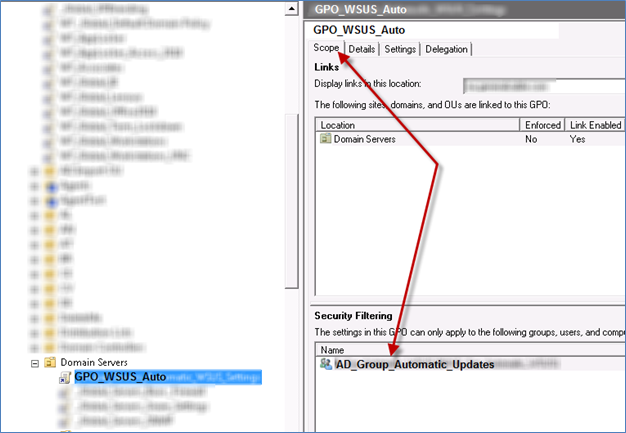
- Create an Active Directory security group (for example AD_Group_Automatic_Updates).
- Add all the server objects that you identified in step 1 to the AD_Group_Automatic_Updates security group.
-
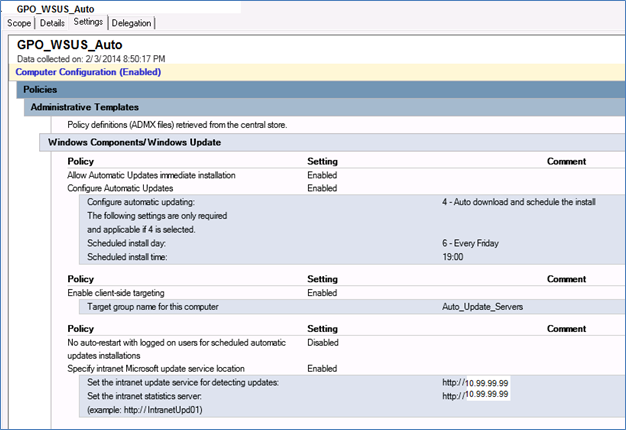
Create a Group Policy Object (for example GPO_WUS_Auto). This will be the GPO that will automatically apply patches and reboot. Below is an example of what this GPO might look like.
-
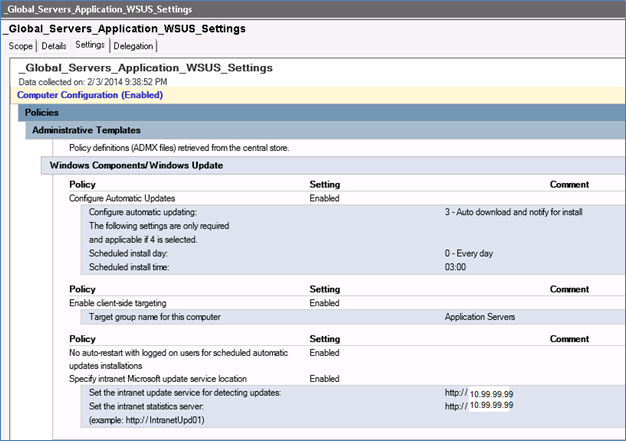
Create a Group policy Object (for example GPO_WSUS_Manual). This will be the GPO that will be applied to all other servers to be patched manually. Below is an example of what this GPO might look like.
- Select the GPO Scope tab and set the security filter to apply this GPO to ONLY the AD_Group_Automatic_Updates security group.
-
Now it is time to specifically DENY the GPO_WSUS_Patches GPO from applying to the AD_Group_Automatic_Updates security group. This can be accomplished by using the Delegation tab. I’ll try and explain this as best I can. Remember, we are assuming that all server objects are located in the Domain Servers OU. Half the servers will receive and apply updates automatically while the other half will not. Therefore you will have two GPO’s linked to the Domain Servers OU:GPO_WSUS_Auto
GPO_WSUS_ManualAs you may or may not know, when you have two similar GPO objects linked to the same OU with like settings, then the last GPO that is applied will overwrite the GPO settings. For example, the GPO_WSUS_Auto group policy will have the Configure Automatic Update setting set to 4 – Auto download and schedule the install. See below.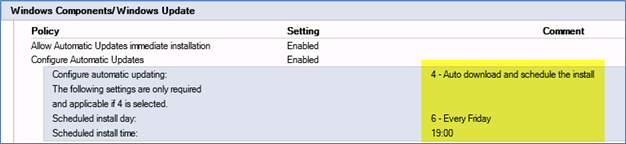
Meanwhile, the GPO_WSUS_Manual group policy object will have the same Configure Automatic Update setting set to 3 – Auto download and notify for install. See below.
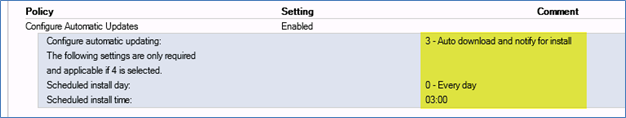
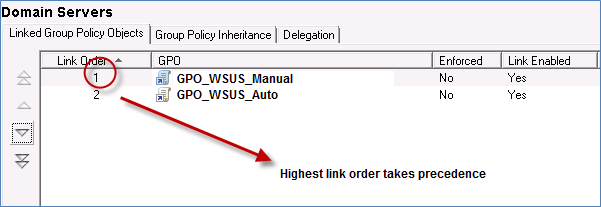
When you have two GPO’s linked to the same OU with the same settings, the one with the highest link order (which is 1) would take precedence. Taking the example below, the setting for GPO_WSUS_Auto would get overwritten by GPO_WSUS_Manual. We do not want this to happen so we can use GPO Delegation to control this. Of course, another way out of this is to separate the servers into separate OU’s. One OU for Automatically patched servers and one OU for Manually patched servers. This becomes messy in my opinion. Who wants to worry about where they place the servers in AD and having to worry if an admin accidently moves a server into the wrong OU. I’d rather control this process using an Active Directory security group such as AD_Group_Automatic_Updates and add my servers to this group. That’s all I have to remember to do if I want a server to be patched automatically. This can be accomplished by properly setting the delegation as I’ve shown in step 8.
-
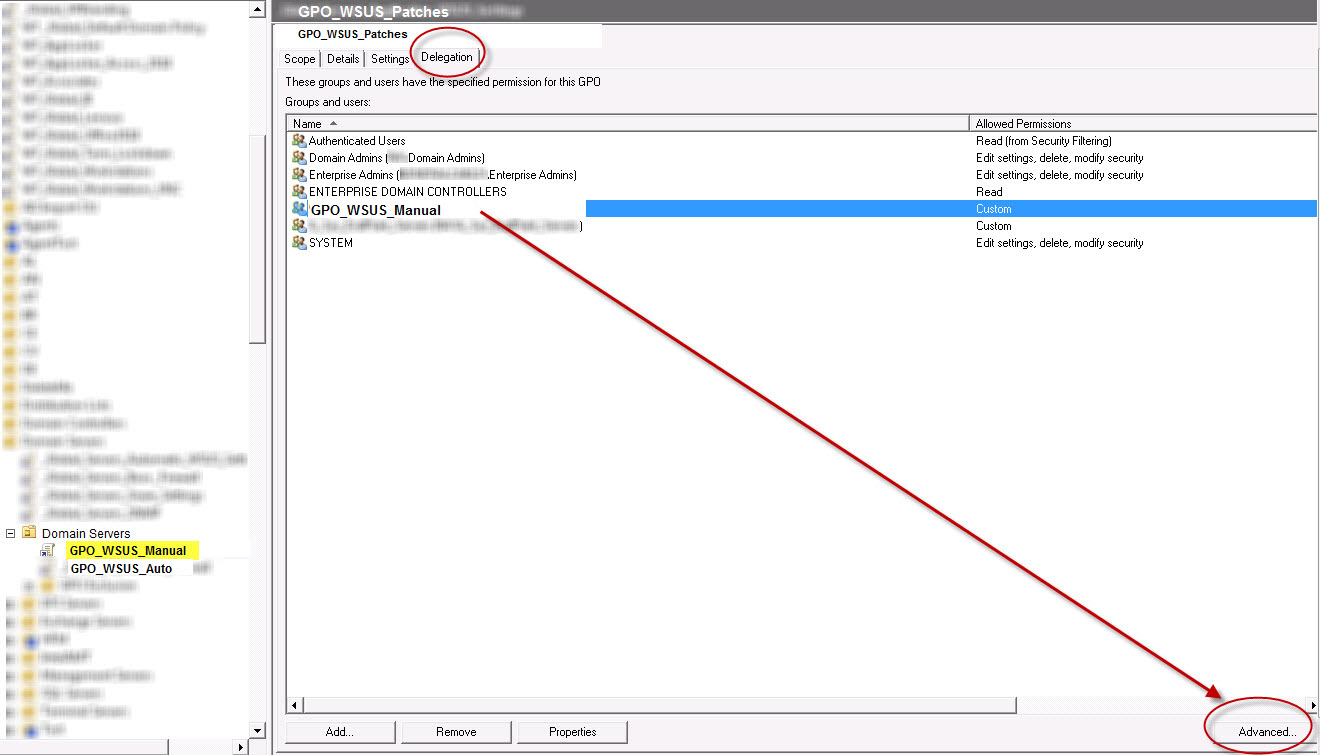
Select the GPO_WSUS_Manual group policy object. Select the Delegation tab. Add the AD_Group_Automatic_Updates AD group using the Add button. Select the GPO_WSUS_Auto GPO from the delegation area and select the Advanced button. See below.
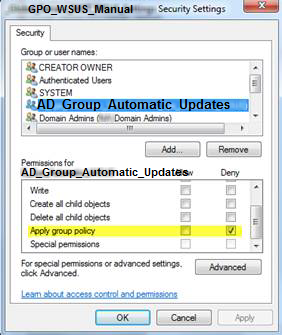
Add the Active Directory group AD_Group_Automatic_Updates and check the Deny column on the Apply group policy (see below). This will prevent the GPO_WSUS_Manual GPO from applying to this AD group.
Now that you’ve added the server to the group, you must make sure the new GPO_WSUS_Auto GPO is being applied. Try running the gpupdate /f command on the server then check the GP results. Make sure the GPO is getting applied by going to Windows Update and checking the settings for running a gpresult /r. If not, try rebooting the server. This always seems to work.
Finally, just because you are now patching half your server automatically, doesn’t mean you shouldn’t check in on them once in a while. Look as your WSUS reports and/or logon to some of the automatic servers to make sure the patches are getting applied. This process has worked very well for me in the past. It has cut down on a lot of manual work as our server count continues to increase. Good luck and happy patching!




Excellent article!!!
Thank you for commenting. I’m glad the article helped.
Question. on step 8 you mention ” Add the GPO_WSUS_Auto GPO using the Add button. Select the GPO_WSUS_Auto GPO from the delegation area and select the Advanced button”. Is this a typo? I don’t see where I can add the Auto GPO into the delegation area, it only allows computers, groups and users. Not GPO objects
William, YES that is a typo! Good catch. I guess my wife was right, I’m not perfect! I revised the post. Thanks for your post, I hope it was helpful.